Syscoin, an instant payment cryptocurrency, has fallen victim to a malware attack after a hacker reportedly inserted a tainted Syscoin Windows client into the project’s GitHub account.
Syscoin Compromised
According to the project’s development team, a hacker replaced the official Windows client with another version containing malware. Users of the software alerted the development team to the presence of the malware in the Windows client when the program started showing up on their computers as malicious.
The tainted Windows client introduced by the hacker contained a malware called Arkei Stealer (Trojan:Win32/Feury.B!cl) — a trojan known for stealing wallet keys and passwords. The project team published a security notice on GitHub, which states:
Upon investigation, the Syscoin developers found that a malicious, unsigned copy of the Windows Syscoin 3.0.4.1 installer was made available via the Syscoin Github release page on June 9th, 2018 due to a compromised GitHub account. This installer contained malicious code. (Trojan:Win32/Feury.B!cl).
The virustotal scan of the malicious file named “re.exe” that is saved to the local temp folder (C:\Users\user\AppData\Local\Temp) upon running the fake installer: https://www.virustotal.com/#/file/b105d2db66865200d1b235c931026bf44428eb7327393bf76fdd4e96f1c622a1/detection
#Syscoin #Security Notice: If you are a Window user and have downloaded syscoin-qt 3.0.4.1 between June 9th and June 13th, please read this now! https://t.co/7hTtobPEKr pic.twitter.com/RVEieXS32l
— Syscoin (@syscoin) June 14, 2018
Risk Exposure and Solving the Problem
According to the Blockchain Foundry team, users who downloaded the Syscoin 3.0.4.1 Windows client between June 9, 2018 (10:14 PM UTC) and June 13, 2018 (10:23 PM UTC) are at risk. The malware reportedly compromises both the 32-bit and 64-bit versions of the client software.
The team advised users to check the installation date of their Windows Syscoin software to see if falls within the time of the hack. If the check turns out to be positive, users are advised to some precautionary steps.
- Perform a full backup of all vital wallet information.
- Run an anti-virus scan to identify and remove the trojan malware.
- Change all passwords used since the time of the hack, preferably on a different computer.
- Transfer funds from unsecured wallets to more secure ones.
The developers themselves also plan to implement some critical steps moving forward to prevent the reoccurrence of such an attack. Team members with GitHub access must enable two-factor authentication (2FA). They must also routinely audit and verify their binaries and signature hashes to detect any form of tampering.
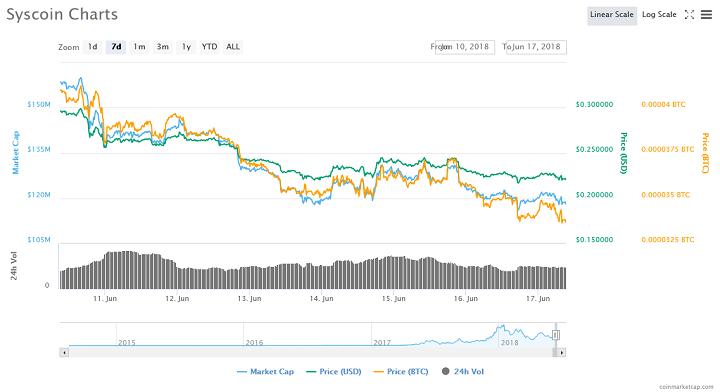
Syscoin is currently the 85th-ranked cryptocurrency, with a market capitalization of $117 million. It is currently trading at $0.22.
What are your comments on the Syscoin hack? Let us know in the comment section below.
Image courtesy Twitter/@syscoin and CoinMarketCap.com.