The growth of Bitcoin over the past four years, together with the recent storm of political revelations on the part of organizations like Wikileaks and Edward Snowden, has brought a renewed interest into developing and promoting the mass adoption of consumer-grade cryptographic technologies. Bitcoin was arguably the first of the trend, giving the user full control over their funds with no trusted third parties whatsoever, and encryption and decryption done on the client side. Since then, we have seen encrypted email replacements like BitMessage, blockchain-based identity systems like Namecoin and even entire encrypted social networks such as Diaspora and tent.io. At the same time, we have seen a trend in making Bitcoin wallets easier to use – first, we had the bulky desktop client Bitcoin-Qt, but more recently we have seen the lightweight desktop client Electrum, numerous mobile phone clients and even in-browser wallets like blockchain.info. Now, however, Kryptokit, a new project released by Anthony Di Iorio and Steve Dakh seeks to combine both trends and take them to the next level.
Enter Kryptokit
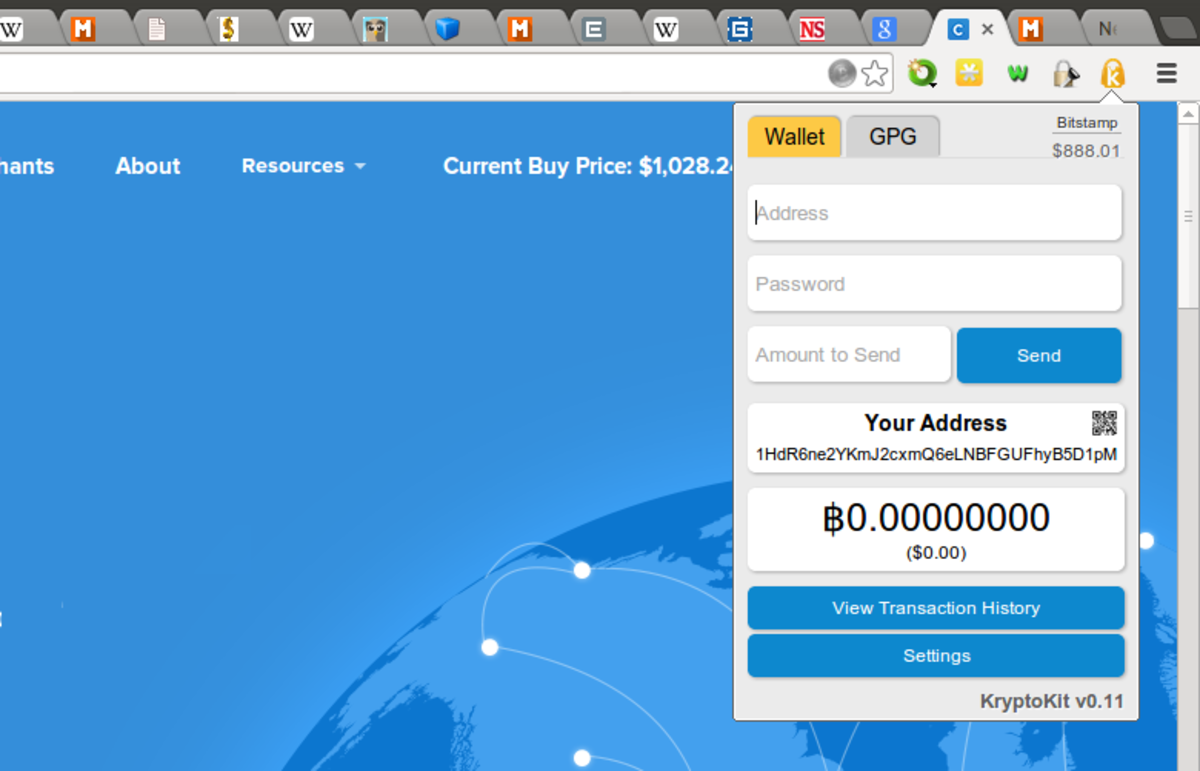
The part of KryptoKit that shows itself to the user at first is perhaps of more immediate practical interest to Bitcoin users: the Bitcoin wallet. KryptoKit takes the idea of blockchain.info’s wallet, which comes packaged as a Chrome and Firefox extension, and pushes it one step further – with Kryptokit, in order to use the wallet you do not even need to open a new tab. Instead, the interface simply exposes itself as a popup from the top right corner of the browser window, allowing users to send and receive bitcoins directly from whatever page they happen to be browsing. In fact, KryptoKit goes even further – every time you go to a new page, the wallet processes the page, captures every Bitcoin address it can find, and lists all of the addresses at the top of the interface. You can then click on any of the addresses in the list to automatically select it.
This is not the first time Di Iorio and Dakh have developed a Bitcoin wallet. Over the past six months, the two have spent a considerable amount of time on another project: RushWallet, an online Bitcoin wallet that has no usernames and passwords. Instead of using usernames and passwords for security, each individual RushWallet account is identifies by a “secret URL”, where the URL itself contains all of the information needed to generate the wallet’s address and private key. This core idea behind RushWallet was not new; a similar “secret URL” based wallet known as InstaWallet had existed since 2011. However, Instawallet faced two major problems, which ultimately proved to be its undoing. First, the funds were stored server-side, rendering all users’ funds vulnerable if the server was hacked. Second, when the user would enter their unique wallet URL in the browser, the URL would naturally go to the server as part of the HTTP request to retrieve the webpage. This information would then, as happens by default, be kept in a server log file. In April 2013, as it turns out, InstaWallet’s server was hacked. Fortunately, the attacker was unable to seize the funds directly, but they did manage to retrieve many URLs from the server’s database, allowing them to immediately proceed to empty a large number of compromised accounts. InstaWallet was quickly taken offline and would never come back.
RushWallet fixes both of these problems. In RushWallet, the funds are stored client side – part of the URL is the seed for the private key, and the Bitcoin cryptography is done using Javascript code executed inside the browser.
The part of the URL that stores the seed in Rushwallet is the “hash” – the part after the number sign. For example, if the URL is http://rushwallet.com/#Hq23BbGtL9Nwu4BARbciZ2bAVBpWVrP8QuemfQQrt1kUyCoy5G, the hash is Hq23BbGtL9Nwu4BARbciZ2bAVBpWVrP8QuemfQQrt1kUyCoy5G.
Because of the way HTTP was designed, the hash part of the URL actually never goes to the server, so aside from quietly and deliberately inserting malicious Javascript code into the application RushWallet itself has no way of accessing the funds. And it worked. “Secret URLs are a proven system,” Di Iorio writes, “and we never had any issues with it.”
Seeing RushWallet’s initial success, Dakh decided that it was time to take the project a step further. “Just a couple weeks ago,” Di Iorio relates, “[Dakh] messaged me that he was working on something new. It turned out to be a Chrome extension. At first it was a frontend with blockchain.info, but then we incorporated RushWallet and it works perfectly now. Deposits and withdrawals are instant, the secure URL system is trustworthy and it works properly.” The wallet is very easy to set up; when a user first loads the wallet, they can securely create a new private key by moving their mouse around to generate random data, although they can also import a brainwallet if they so choose. From there, the wallet simply functions as any other ordinary Bitcoin wallet would. The security model works just like Rushwallet; “credentials are stored client-side, so nothing goes to the servers,” Di Iorio says. And now, after weeks of development and testing, Di Iorio and Dakh are ready to finally release their wallet to the public.
“Enkrypted” Messaging
However, despite its unprecedented ease of use, the wallet is arguably not even the most impressive part of Kryptokit. That honor goes to the other tab of the extension: the encrypted messaging interface. The messaging interface is based on GPG, a popular open-source implementation of the original PGP protocol invented by Paul Zimmerman in 1991, which is still the gold standard of secure email today. KryptoKit functions as a fully self-contained GPG platform, allowing users to create new GPG keys inside the interface, but one can also import an existing key from other PGP/GPG applications such as Enigmail.
Once a user has a private key inside KryptoKit, the user can then ask their friends for their public keys, and load the public keys into KryptoKit. Once two users have each other’s public keys and their own private keys loaded into KryptoKit, they can encrypt messages for each other, and send the encrypted messages through the application. The encryption is handled seamlessly; once KryptoKit is set up, all that a user needs to do is write the message, select the recipient, enter their password and click “Send”. The recipient will then immediately see a notification that they have a new message, and will be able to view it, entering their password to unlock their private key so they can decrypt the message. The decryption, once again, is seamless; once the recipient clicks “View message” and enters their password, they will simply see the message appear in unencrypted form in a popup.
Aside from perhaps the unfamiliar aspect of users needing to ask their friends for a public key, KryptoKit offers what is literally the simplest possible interface for GPG encrypted messaging that one can create. Users need to enter their password to send and receive messages, but aside from that all of the cryptography is handled automatically inside the application. In theory, applications like Enigmail, a plugin that seamlessly integrates GPG encrypted email into the popular desktop mail client Thunderbird, have existed for years; in practice however, fewer and fewer people use desktop mail clients every year, and the ease of use of simply installing a browser extension and having everything “just work” is unprecedented. Even among users who do not care about encryption, the concept of having a messaging app in the top right corner of their own web browser is by itself a powerful feature, so KryptoKit has a serious potential to take off even among less technical users to a much greater extent than previous applications like Enigmail.
One possible suggestion for KryptoKit to target the non-technical market even further is to improve the one aspect of the application that is still unintuitive: the key management. Ideally, KryptoKit would include an interface to public key servers such as those at Maiz and MIT, and perhaps even the decentralized key server that is the Namecoin network, so that users can simply search for their friends’ names inside of the application and have the public key downloaded from the key server and imported into KryptoKit automatically. The app would also, of course, provide the opposite functionality – allowing users to upload their keys to Mainz and MIT’s keyservers from inside the application. At that point, KryptoKit may even choose to remove all references to “encrypted” inside the application – it would simply be a messaging app that requires a password, and the key management would be in the background, accessible to those advanced users who are interested in working with the lower-level cryptographic details, and otherwise simply serving as a passive reassurance that the messaging is secure.
There are also plenty of other directions in which KryptoKit can go much further, and the developers themselves have stated that many of these improvements are already planned for future versions of the software. The first obvious next step is to offer, in addition to its current email-style messaging platform, a chat interface, perhaps using the OTR protocol instead of plain GPG. OTR has the advantage that it is possible to send a message “off the record” (hence the name) – although the recipient certainly can copy the sender’s message and paste it to whoever they want, the protocol is designed in such a way that the recipient will not be able to prove to anyone else that it was the sender who sent the message. From there, other forms of communication are also feasible; voice and video communication is perhaps next in line. Finally, the last step would be to include a fully fledged social network, that would also serve as a decentralized marketplace with a functioning reputation system. Altogether, Di Iorio summarizes, “you [would] have a social network that is secure and encrypted and is also a payment mechanism, all in a file less than 1 MB”.
In the near term, however, there are also other, more general, priorities that Di Iorio intends to address. “The next step is to put the community behind this,” Di Iorio explains. “We could put bounties for people to either add functionality or put $10000 behind some private key [as a challenge to locate security vulnerabilities].” For monetization, Di Iorio reassures users that he will definitely keep the app free. “It’s about getting numbers and people using it,” Di Iorio explains. Instead, he says, “we could localize an ad spot at the bottom of the extension. If you’re in Canada, it would be a link to CaVirtex, or localbitcoins. If we were to do it that way, we would actually be adding value in the ads.”
And his claim is correct; given that the GPG feature of KryptoKit by itself will be enough to attract many users, the app may well introduce new users to Bitcoin, and they would benefit from having an easy link to a local exchange where they can buy bitcoins. But even without any of these features, KryptoKit is here, now. It offers a highly user-friendly and efficient Bitcoin wallet, and its messaging app can be set up within minutes. If you already use encrypted email, you can even import all of your friends’ public keys right away. If either of these features interests you, you should consider downloading KryptoKit and starting to use it today.