Security is becoming more and more important in recent years,a s technology evolves at an accelerated pace. Most people use various services and platforms every day, without taking proper precautions to keep their information safe. Storing a secret crypto key in the cloud has never been a bright idea, and it was only a matter of time until a new type of attack was developed to steal this data.
Also read: Jeb Bush Wants to Repeal FCC Net Neutrality Regulations
Amazon’s EC2 Platform Vulnerable To Crypto Key Theft
Despite there being multiple cloud-based storage solutions on the market right now, most people will use Amazon’s EC2 platform. Due to its relatively cheap price, and ease-of-use in terms of setting up, Amazon’s EC2 has grown its international customer base over the years. But once again, the matter of platform security might throw a monkey wrench into Amazon’s plans.
It is not the first time Amazon and their EC2 platform are being confronted with a proof-of-concept attack. as a previous key-recovery attack on co-located virtual machines was discovered in 2009. Virtual machines and cloud storage have always been a focal point for attackers and hackers, as most of these services are not as secure as they want everyone to believe.
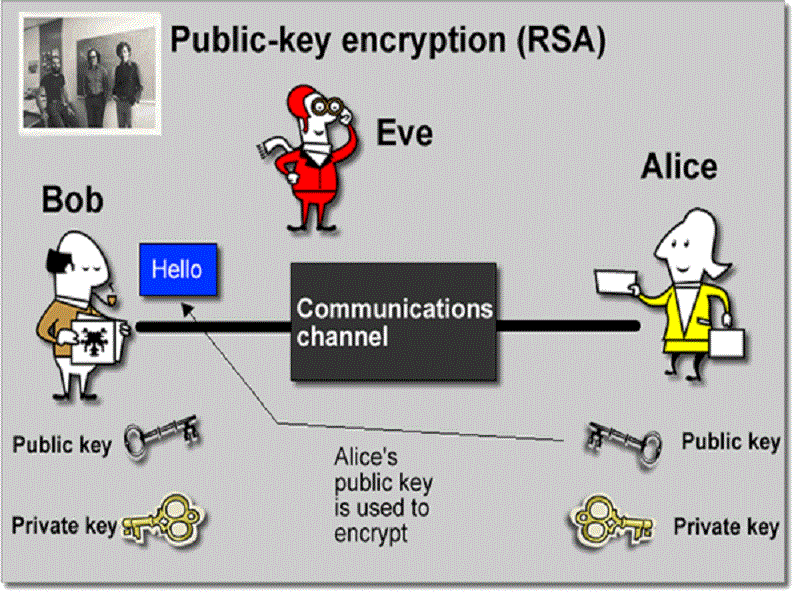
Even though security researchers and cryptography experts have put in a lot of hard work to fix the 2009 attack vector, it looks like that wasn’t the only vulnerability that needed to be patched. Any full private key used in a modern implementation of the RSA cryptosystem is now vulnerable to attack. To pull off this attack, a CPU cache attack between two Amazon [EC2] accounts is executed, as long as they are on the same chip or chipset.
Exact details of this new attack against Amazon EC2 services has been documented in a research whitepaper. The worrying part about this vulnerability is how other crypto app s and libraries are also vulnerable to this attack. However, pulling off a successful attack does require a lot of luck and expertise. Security experts are not expecting to see a widespread usage of this exploit in the near future, but a solution has to be found sooner or later.
s and libraries are also vulnerable to this attack. However, pulling off a successful attack does require a lot of luck and expertise. Security experts are not expecting to see a widespread usage of this exploit in the near future, but a solution has to be found sooner or later.
Bitcoin Passed on RSA and Used ECDSA Encryption
There is a good reason why Bitcoin was developed using ECDSA encryption, and not the RSA standard. ECDSA encryption offers the same level of security as RSA does, but leaves a much smaller footprint. Furthermore, as more security precautions are added to RSA, the larger the private key becomes.
Bitcoin is a system developed to send small packets of data around at all times, due to its peer-to-peer nature. On the other hand, ECDSA signature verification is slightly slower compared to RSA, but that one minor benefit should never outweigh the vulnerabilities faced by RSA encryption. StackExchange has a lengthy thread for a more detailed comparison between ECDSA and RSA.
What are your thoughts on this new RSA vulnerability? Do you see a potential solution to this problem? let us know in the comments below!
Source: Ars Technica
Images courtesy of Amazon EC2, RSA, Shutterstock