U.S security firm Trend Micro has discovered a Monero crypto-mining attack targeting Linux Servers. The latest attack has been linked to an earlier $3 million USD Windows hack.
According to the Trend Micro report, a group has taken advantage of a vulnerability in the Network Weathermap plugin for Cacti. The open-source visualization tool is widely used by ISPs, internet exchanges, telecommunications networks, and Fortune 500 companies to map network activity.
Hackers Have Made $75,000 USD So Far
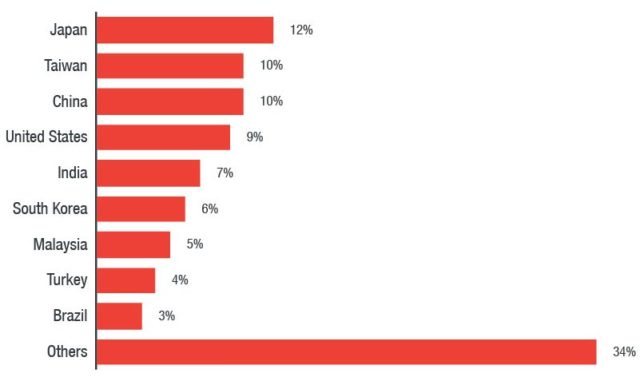
Trend Micro’s Smart Protection Network indicates the hack is still ongoing and primarily affects Network Weathermap users in Japan, Taiwan, China, the U.S, and India. It has discovered two Monero wallets receiving funds from the hack totaling illegal crypto-mining returns of $74,677 as of March 21st, 2018.
The Network Weathermap attack has been connected to an earlier hack which used JenkinsMiner malware on Windows machines and made hackers at least $3 million USD in Monero.
Trend Micro believes that the hackers may have taken advantage of a security flaw and a delay in the Network Weathermap owners “patching”, or updating, of their open source tool:
It’s possible these attackers are taking advantage not only of a security flaw for which an exploit is readily available but also of patch lag that occurs in organizations that use the open-source tool.
The hackers are exploiting CVE-2013-2618, a five-year-old vulnerability in the Network Weathermap system. They have exploited the flaw to gain code execution ability on the underlying servers, installing a customized version of legitimate mining software XMRig. The report explains:
It’s also a classic case of reused vulnerabilities, as it exploits a rather outdated security flaw whose patch has been available for nearly five years.
Users May Still Be Inadvertently Mining Monero
As the hack is ongoing, users of the Network Weathermap tool could still be inadvertently mining Monero, which is then being transferred to the hackers’ Monero wallets. According to Trend Micro, victims of the attack will be running Linux x86-64, Cacti, and the outdated Network Weathermap plugin with open access to an internet connection.
Monero Is the Hacker’s Coin of Choice
Monero is the most anonymous of the leading cryptocurrencies and as such is utilized widely in attacks of this nature. Monero coins do not have any identifying attributes, all coins are the same. Stolen, or illegally mined coins cannot be blocked by exchanges or wallets. Monero user addresses are also hidden by Monero’s use of ring signatures and stealth addresses.
Do you use the Network Weathermap tool? Have you been an inadvertent victim of a cryptocurrency mining hack? We’d like to hear your comments.
Images courtesy of iStockPhoto, Trend Micro